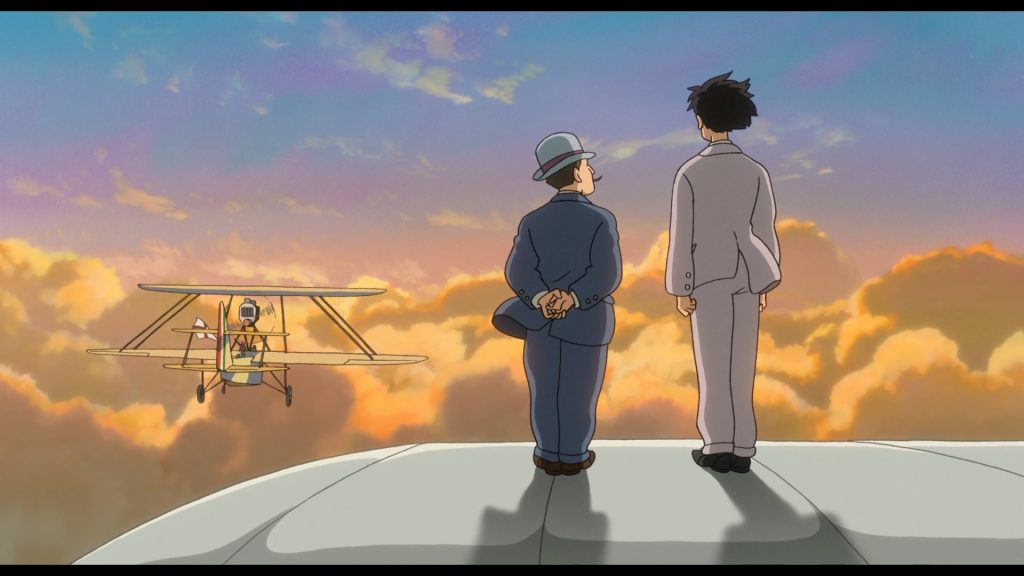
“We have hope. Rebellions are built on hope! ” – Jyn Erso
Now that’s a Star Wars I like to see!
Without hesitation the best Star Wars movie of the last decade (as of Jan. 2017). That’s not a hard feat though I must admit. But it brought far more to the cinematic universe of Star Wars than the last “Episode”. Not in the holes it fills, but more in the quality of the story, movie and its overall originality.
Now I can hear some of you screaming in the back, that’s not part of the main nonalogy (nonalogy? nonology? ennealogy?), it’s a standalone movie, it’s not really Star Wars. Well, tell you what, I don’t care. Disney decided to go non-canon anyway, so for me it’s just another movie in the alternate Star Wars universe.
Now that’s probably a targeting strategy for all of us who thought that Force Awakens was more of a disgrace than Ep. I, II, III. But it worked, I liked it, and now I want to see the next episodes. You got me Mickey Mouse!
The opinions were not undivided, but I liked it. There is something to this movie that is more human and makes it more plausible compared to the others in the series. It’s about small things. Like the stains and dust on spaceship windows, hyper-space light reflections during hyper-drive, the actual need of hyper-drive, the actual need of space travel, the reality of occupation by the Empire. In the end it made the movie much more believable to me.
But one of the things that I really liked was the way Jyn Erso character was developed throughout the movie. You could grasp her complicated views on the Rebellion and the Empire. You could feel her fears and doubts, you could see her think, understand her own awareness of the events and her place among them. She appeared as human as you can be. So it was really natural for me to attach to her character. And all that contributed to my realization that, in the end, she displayed real courage. See, you love people for what they really are, their inner self. And the movie tried to emphasize just that, what she really is.
It also presented the more hazy face of the Rebellion and the Empire by displaying both factions as more organic entities with their own internal political struggles, conflicting ambitions and ideals. This resulted in a story that had a bit more to offer by detaching itself slightly from the manichaean vision of the episodes.
It was also beautiful and thrilling. The pace was really good, and it contributed a lot to the intensity of the movie, especially in the latter parts. In the end all that contributed to a story that was most of the time really enjoyable.
Now that’s not to say that the movie was without flaws.
First, the most obvious, resurrecting dead actors with completely CGIed characters, just forget about it, seriously! It does not work yet, like not at all. Peter Cushing looks like some kind of evil puppet that suddenly became self aware but still has a really hard time figuring out what it is to behave, move and talk like an human being. Carrie Fisher was fine, but only for the fact that you see her for a couple of seconds.
“USE-THE-FORCE-LUKE”
A robotized version of Sir Alec Guinness plays Obi-Wan Kenobi in a future Star Wars installment.
– Robby the Robot portrait by Iain Claridge
The movie tries hard not to fall into the SixFlags camera shooting syndrome (where some scene look more like they were filmed from a rollercoaster than anything else) or the far too common InYourFace syndrome trying to abuse the sensational. Sure some scenes will make you cringe a little, but it’s still not as bad as The Hobbit for instance.
There are the obligatory two cents jokes and somewhat not-always-that-subtle cameos. But there are some who apparently think that you cannot make a movie without those nowadays. While I’m OK with nods to older episodes as long as they do not show up too frequently to feel like distractions, putting a stupid not funny at all joke at the end of a 30 seconds action scene can ruin not only the scene, but also the characters and butcher the story credibility.

Lastly I think that the movie really has one big flaw, it’s its non-homogeneous way of handling the characters. Like I said Jyn Erso character is well developed and this really adds to her credibility. Others like Cassian Andor or Cpt. Obvious (K-2SO) are also fine, and the latter makes a nice and funny support character.
On the other hand some characters were developed on a completely different dimension. I think in particular of Chirrut Imwe and Baze Malbus. They did not add that much to the plot, they got some of the worst and almost all clunky lines, and I couldn’t help but to see them as a dead weight couple that somehow found himself playing in the wrong movie.
I may seem a bit harsh but I really think you shouldn’t add characters just for the sake of it. Even so with the laudable intention of completing the story by the addition of new components. The story that the movie tries to convey must act as a coherent whole. And in this case it could have been much better articulated over fewer characters.
That being said I’m now eagerly waiting for the next episodes. With a bit of apprehension though considering Rian Johnson (Ep. VIII) and Colin Trevorrow (Ep. IX) filmography. Looper left me a bit unimpressed and that habit of throwing successful TV series directors or writers (even when that was only for a handful of episodes) in charge of tent poles movies never turned out well for me. And don’t even get me started on Jurassic World. But in the end only time will tell!